WPA enterprise allows 8021.x RADIUS authentication. I have always wanted to try out certificate based authentication in Wifi networks (EAP-TLS). I have tried many methods, probably this is the easiest way if you have a mikrotik router. Otherwise you may need to deploy something like FreeRADIUS. Here will be configuring the mikrotik router as RADIUS server and our access point(s) as client. This will be very helpful if you have a SOHO and have different OEM access points.
Note: do not touch the default RADIUS option in miktoik. We will do everything from user-manager package.
1. User-Manager Package
Download User Manager Package from mikrotik site (double check the version and architecture) and install it. Complete documentation about the package is in mikrotik site. In short it is a user manager with inbuilt RADIUS server.
Check out the usage of the package in-depth. It has ton of other features which I have not mentioned.
2. Generating the Required Certificates
Create CA, certificate for user-manager and user from routeros terminal.
# Generating a Certificate Authority
/certificate
add name=radius-ca common-name="RADIUS CA" key-size=secp384r1 digest-algorithm=sha384 days-valid=1825 key-usage=key-cert-sign,crl-sign
sign radius-ca ca-crl-host=radius.spacex
# Generating a server certificate for User Manager
add name=userman-cert common-name=radius.spacex subject-alt-name=DNS:radius.spacex key-size=secp384r1 digest-algorithm=sha384 days-valid=800 key-usage=tls-server
sign userman-cert ca=radius-ca
# Generating a client certificate
add name=k-client-cert common-name=k@spacex key-usage=tls-client days-valid=800 key-size=secp384r1 digest-algorithm=sha384
sign k-client-cert ca=radius-ca
# Exporting the public key of the CA as well as the generated client private key and certificate for distribution to client devices
export-certificate radius-ca file-name=radius-ca
# A passphrase is needed for the export to include the private key
export-certificate k-client-cert type=pkcs12 export-passphrase="your secure pass phrase"
# Please check this for exporting in android - https://stackoverflow.com/a/73512646
# the -legacy flag is important
#https://help.mikrotik.com/docs/display/ROS/Enterprise+wireless+security+with+User+Manager+v5
#Important: Read the above link throughly. Do not Skip. The common-name, in my example .spacex (.mikrotik.test) should be present in user certificates.
#Otherwise you will break heads, it just won't work.
3. Configuring User Manager
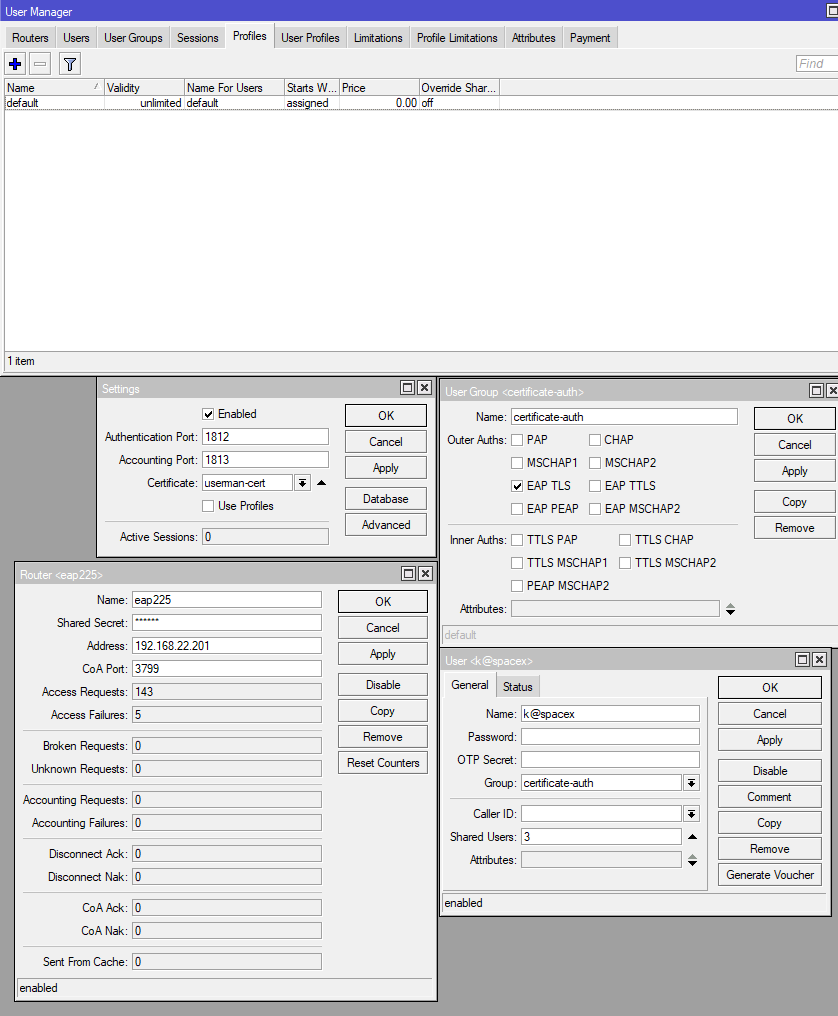
-
Profiles tab: Create a default profile from GUI / terminal if not already present.
-
User Groups tab: Create a new user group with
certificate-authas name and choose onlyEAP-TLSas authentication method. (you can also choose other methods which require a password also) -
Users tab: Create a new user
k@spacexwith groupcertificate-auth. -
Routers tab: In settings tab check
enabledand choose ouruserman-cert. Leave ports to default. -
Routers tab: Add a new router. Enter a name and IP address of yor access point. Remember the shared secret, which you will need to enter in your access point. (you can add as many as you want)
4. Configure Access Point
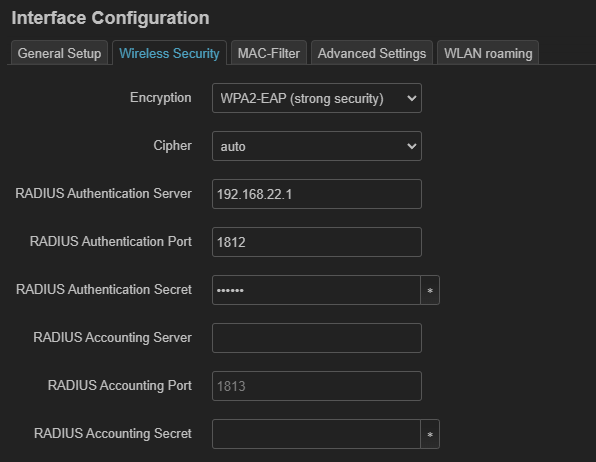
-
These widely vary from software you are using. But basically you need to choose
WPA2-Enterpriseauthentication in your access point to enter RADIUS server IP (IP of mikrotik router) and shared-secret. -
I have tested it in my tp-link EAP225 running on both tp-link firmware and open-wrt and works fine.
5. Configure Clients
Add the k-client-cert or whatever name you have give to clients like your mobile and windows. Just a simple search will show many tutorials on how to do it. I have not had any problems expect in android which needed the certificate in legacy p12 format (refer step-2).
Done!
Connect the wifi SSID, when prompted choose the certificate installed in client.
6. Reference:
https://help.mikrotik.com/docs/display/ROS/User+Manager
https://prog.world/how-to-make-wi-fi-mikrotik-and-tp-link-friends-using-radius/
https://help.mikrotik.com/docs/display/ROS/Enterprise+wireless+security+with+User+Manager+v5
https://github.com/multiduplikator/mikrotik_EAP
https://www.tp-link.com/us/support/faq/500/
https://openwrt.org/docs/guide-user/network/wifi/encryption (wpad package in open-wrt for WPA-enterprise. you need to remove all wpad-* packages and install just wpad)